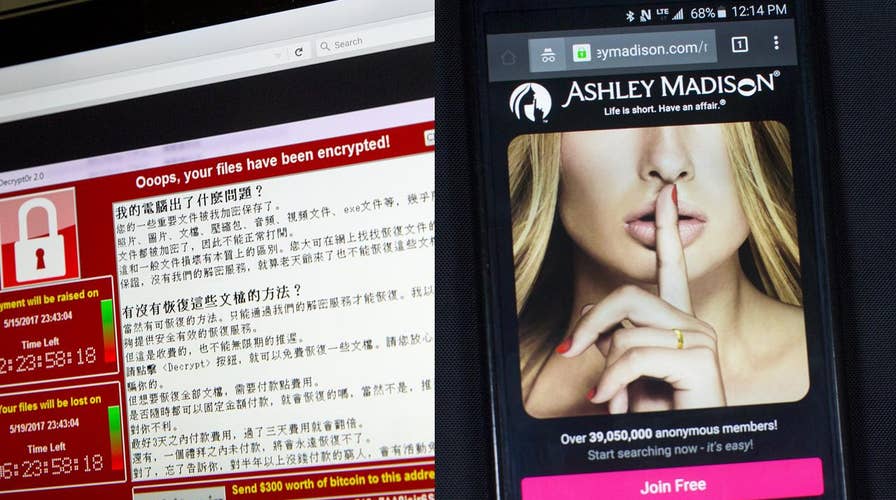
World's biggest cyberattacks: 'Wannacry' to Ashley Madison
Recent cyberattack 'Wannacry' spanned across 150 countries around the world, but how does it compare to other massive hacks? A look back at some of the biggest and costly data breaches in the world
A massive worldwide cyberattack over the weekend crippled government and infrastructure in more than 150 countries — including Britain’s hospital system and Germany’s railways — in what is expected to be the largest online extortion attack ever recorded.
Rob Wainright, director of the Netherlands-based Europol, called the global reach of the attack “unprecedented and beyond what we have seen before.”
“At the moment, we are in the face of an escalating threat. The numbers are going up,” Wainright said. “I am worried about how the numbers will continue to grow when people go to work and turn on their machines on Monday morning.”
Hundreds of thousands of computers were infected by the ransomware cyberattack — in which hackers extorted users for currency to unencrypt their data — in more than 150 countries, according to the BBC.
While this weekend’s attack could be the largest to date, cyber crime has been on the rise in recent years, according to a 2016 report from PricewaterhouseCoopers, a global professional services organization that deals in cybersecurity and privacy, among other issues.
PwC’s study found that the number of cyber security incidents across all industries increased by 38 percent in 2015 — the biggest increase in 12 years.
MORE VICTIMS EXPECTED MONDAY IN MASSIVE 'WANNACRY' CYBERATTACK
“Cyber criminals are becoming more industrialized and more organized,” Derk Fischer, a partner with PwC in Germany who deals in the delivery of cyber security assessment and consulting services, said in a statement. “What we’re seeing is the emergence of a new kind of ‘industry sector’ that thrives on the complex connectivity that characterizes the Internet.”
And a 2016 report from Verizon and security company McAfee found that cyberattacks involving ransomware increased 50 percent. Among those targeted by ransomware attacks, government organizations are the most frequent, the report found, followed by health care businesses and financial services.
Elections
A 2016 White House audit found that the U.S. government was hit with more than 77,000 “cyber incidents” in the fiscal year 2015 — a 10 percent increase from the previous year.
And the U.S. Department of Homeland Security said last year that the number of cyberattacks targeting industrial control systems for automated industrial machines is on the rise, Business Insider reported.
But it was the hacking of the Democratic National Committee’s emails that is perhaps now one of the most infamous and disputed cyberattacks in recent U.S. history. U.S. intelligence officials have accused the Russian government as the catalyst behind the hackers in an effort to influence the 2016 presidential election.
“There shouldn’t be any doubt in anybody’s mind. This was not something that was done casually, this was not something that was done by chance, this was not a target that was selected purely arbitrarily,” Adm. Michael S. Rogers, the director of the National Security Agency and commander of United States Cyber Command, said at a postelection conference, according to The New York Times. “This was a conscious effort by a nation-state to attempt to achieve a specific effect.”
Russian officials have denied involvement.
While one type of cyberattack isn't necessarily more dangerous than another, what seperates the DNC hack from WannaCry ransomware attack over the weekend is the scale of the more recent hack, renowned cybersecurity expert and George Washington University professor Dr. Diana Burley told Fox News.
"The attack on the DNC was specifically to get information," Burley said. "This particular attack, at least what we've seen so far, is not related to stealing information per se, but rather gaining control over people's systems so that they could then ransom back access to them."
"It's all dangerous — whether we're talking about stealing information or locking people out of systems and computers. It's all a problem," she continued.
Cybersecurity experts also linked Russia to the hack into the campaign of French President Emmanuel Macron. Just as the midnight deadline that halts campaigning in the French election passed, tens of thousands of internal documents and emails from Macron’s campaign were released, including some from personal Gmail accounts, according to The Guardian.
Experts believe the hackers behind the cyber breach are linked to those behind the DNC leaks, the Guardian reported.
Blackouts
Russia, too, was blamed for darkening the Ukrainian capital of Kiev in December 2016 — though through a different type of cyberattack.
Power supplier Ukrenergo said at the time that an analysis indicated a “premeditated and multi-level invasion,” according to Reuters.
Marina Krotofil, a lead cybersecurity researcher who assisted in the investigation into the power outage, said the incident was “intentional” but “not meant to be on a large scale.”
“They actually attacked more but couldn’t achieve all their goals,” Krotofil said.
The 2016 blackout that lasted for more than an hour was harkened to another attack in 2015 that left 225,000 people in the dark in western Ukraine. Then, in what Reuters called the “first-of-its-kind cyberattack,” hackers were also able to damage power distribution equipment which complicated power restoration efforts.
That attack was widely blamed on Russia by Ukrainian security services.
Ukranian President Petro Poroshenko also blamed the 2016 outage on Russia and alleged that the neighboring country was waging a cyber-war, the BBC reported. Aside from the blackout, Poroshenko alleged hackers had targeted state institutions about 6,500 times at the end of 2016.
“Acts of terrorism and sabotage on critical infrastructure facilities remain possibly today,” he said.
GLOBAL RANSOMWARE ATTACK HITS 'LIMITED NUMBER' OF US COMPANIES, DHS SAYS
However, in the global WannaCry attack over the weekend, Russia was one of the countries that fell victim. Kaspersky Lab, a Russian antivirus company, reported that Russia was the hardest hit in the first wave of attacks as it infected more computers there than anywhere else, according to The New York Times.
Infrastructure
For nearly a decade, a hacking group in Shanghai reportedly breached more than 100 U.S. companies and stole valuable data, according to a 2013 report.
The hacking — which was billed as one of the largest hacks at the time — was conducted by a group called the Comment Crew and ATP1 linked to the China’s People’s Liberation Army who stole data from 2006 to 2014, Wired reported.
Comment Crew focused on companies that are instrumental to American infrastructure, including information regarding the U.S. power grid, gas lines and waterworks, the New York Times reported, citing a detailed study of the hacking group by Mandiant, a U.S.-based computer security firm that directly implicated China in the cyber breach.
HOW TO PROTECT YOURSELF FROM RANSOMWARE
According to Wired, the hackers used “tried-and true” methods to obtain access to victims’ information, including spear phishing emails and custom digital weapons.
“They employ good English — with acceptable slang — in their socially engineered emails,” Mandiant said in the report. “They have evolved their digital weapons for more than seven years, resulting in continual upgrades as part of their own software release cycle. Their ability to adapt to their environment and spread across systems makes them effective in enterprise environments with trust relationships.”
Chinese officials denied involvement in hacking, the New York Times reported.